Self-Defense and Secure Communications

While pointing to resources for further study and giving pointers on what the risks of using computers and cell phones are, we have historically veered away from recommending certain technology. This was partly due to a desire to prevent the state from building a profile of the technologies that we rely on, and partly because there are organizations more focused on these questions that will have more up-to-date and in-depth information to offer. While the latter is still true, there are a few technologies that are so standard that we see little risk in mentioning them by name.
Another thing we want to touch on here is imposing higher standards for our electronic communications from other revolutionary organizations. Recent communications we’ve received have reinforced to us the need for diligence in having secure communication networks. So let us begin with some basic principles.
Assuming that we have a practical interest in developing communications with another revolutionary organization, there are three political questions that we must ask about the organization: 1) what is their political line? 2) what practice can we see to prove they are consistent in implementing that political line? 3) can we confirm that we are talking to someone that represents the organization? Once we decide to communicate with an organization we must then be concerned with who knows that we are communicating and who knows what we are saying to each other.
On our website we have our public email address, a form to submit anonymous messages, and our public GPG key to encrypt messages to us. Our website has been online for over 5 years and has material dating back that far demonstrating our work and our political line. We believe this is a good model that would allow another group to confirm who we are and communicate with us securely and anonymously via the internet.
The downside to the public email address is that it is easily targeted for monitoring, allowing the state to know who is contacting us. This is why we have the anonymous form and why we tell people to email us from addresses that are not linked to them persynally. For prisoners, one may think that one’s mail is monitored anyway, so emailing is no greater risk than sending a letter. However, there is an increased risk in that digital communications provide for permanent documentation of who you communicate with and what you say, allowing for easy data mining of that information later. This is possible with snail mail, but it requires more effort by the state and is not done consistently; at least for most people. Emailing is convenient, and is a fine way for prisoners to contact us, but be aware of the increased ease of surveillance. If you are using non-state-sponsored technology, then you should consider using the tools we mention below if you have access to them.
For other revolutionary organizations, if our only communication is via anonymous email then we need a way to confirm who you are. Having an established website with your public email address and public GPG key on it and then using that GPG key to encrypt all email is a way to do this. GNU Privacy Guard (GPG) encryption should be used for all communications. Not only does it prevent a snooper from reading intercepted messages, it allows the receiver to confirm the identity of the sender if they have a trusted GPG key from that party. Email addresses are easy to spoof, while it is practically impossible to spoof GPG signatures.
One of the documents we link to on this subject is titled Surveillance Self-Defense. We think this is an appropriate title, and we need comrades to think beyond fists and guns when they think about “security” and “self-defense.” Even if you don’t use computers or cell phones at all, then you must have a basic understanding of the risks to come to that decision (unless you are in prison and have no choice in the matter). While martial arts are great in many ways, we do not see hand-to-hand combat as a decisive aspect of the struggle at this time. And since we have assessed our strategic stage to be one where armed struggle would be a fatal mistake, we do not require or promote weapons training. We do require regular study, review and practice of anti-surveillance technology of our members. And we hold those we relate to to similar standards. The worse your security practice, the more risk you are to us, and the less we will interact with you. Simple as that.
While being effective in self-defense requires further study than this
document, we want to give some simplified recommendations here to get
people started:
-
When you carry a cellphone it is easy for the state to know where you
are and to electronically record sound and even video of your
surroundings, even if your phone is off
-
Encrypt your data, if possible encrypt your whole drive including your
operating system; there are different tools to do this effectively, but
TrueCrypt is a popular
cross-platform tool
-
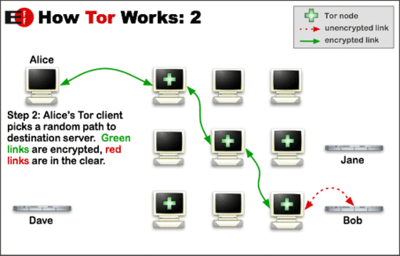
When connecting to a website or your email you can be identified by your
IP address; the best way to hide this is through The Onion Router via
the Tor
Browser Bundle, the TAILS
operating system or
Orbot for Android
cell phones
-
As discussed above use GPG to encrypt messages and confirm who messages
are from
Of course, prisoners using state-owned computers will not have the option to use any of these technologies, so it is mostly just a question of using email or snail mail. But if you are looking forward to a release date and hope to keep in touch with MIM(Prisons) then it would be worth learning more about these technologies and tactics to protect yourself.
How we approach self-defense is very much informed by our political line. Our line leads us to focus more on the First Amendment than the Second. But ultimately there are no rights, only power struggles. Currently, we do not have the ability to defend the movement militarily, but we do have the ability to defend it with a well-informed electronic self-defense strategy. And just as computer technology, and the internet in particular, was a victory for free speech, it has played a role in leveling the battlefield to the point that the imperialists recognize computer warfare as a material vulnerability to their hegemony. The Obama administration has gone so far as to call journalist Julian Assange a “terrorist” after WikiLeaks published documents that the United $tates did not want the world to see.(1) As the means of production advance, we must learn to utilize the emerging technologies for both offense and defense in the interests of the international proletariat.
- Loved Ones Fight Santa Barbara Ban on Letters to Prisoners
- Global Telecom Monitoring for Global Domination
- NSA Hacking Google and Yahoo Data Centers Reveals Broad U.$. Government Spying
- Documents Reveal Imperialist Spies' Online Attacks on Activists
- Secure Communications is Key to Organizing the Lumpen
- Beware of Gang Intelligence in New York
- Feds Ban MIM(Prisons) on CorrLinks, Disregard 1st Amendment